Google Patches Sixth Chrome Zero-Day Exploited in 2025 Attacks

Google has released an emergency security update to fix a new zero-day vulnerability in its Chrome web browser, marking the sixth actively exploited flaw patched this year. The Vulnerability Security Update Zero-Days in 2025 This latest fix adds to a growing list of Chrome zero-days exploited this year: In 2024, Google patched 10 additional zero-day […]
How attackers are still phishing “phishing-resistant” authentication
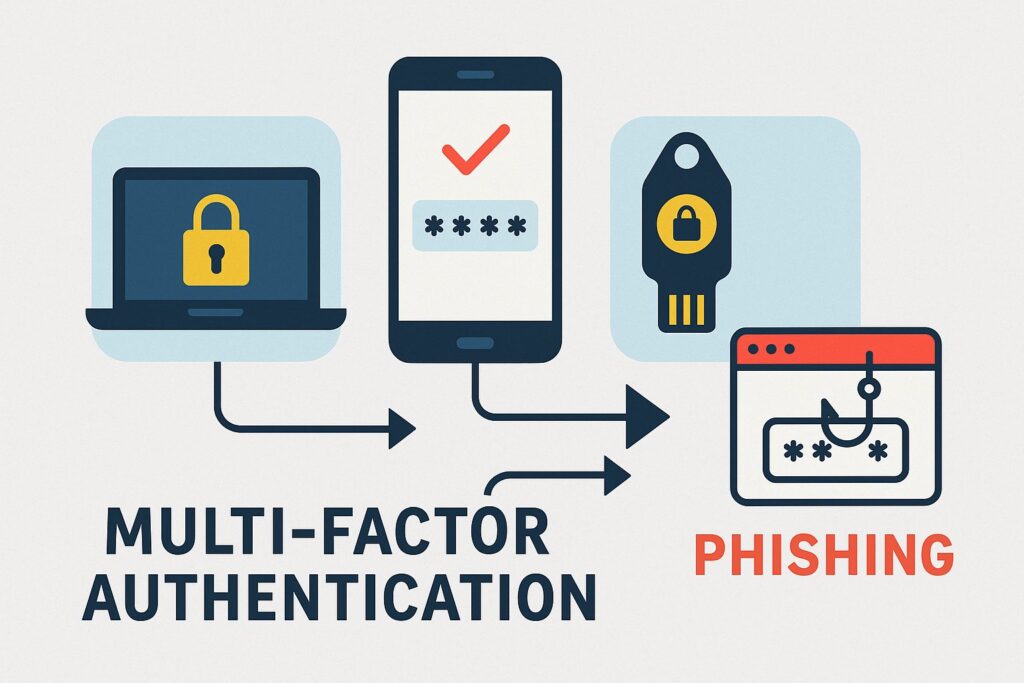
🔐 Overview Despite the rise in phishing‑resistant authentication methods such as FIDO2-based passkeys, WebAuthn, Windows Hello, and physical security keys attackers continue to successfully bypass them using more sophisticated phishing techniques. 🧪 Attack Techniques Used 1. Downgrade Attacks 2. Device‑Code Phishing 3. Consent Phishing (OAuth Abuse) ⚖️ Why These Methods Still Work ✅ Mitigation Strategies […]
16 billion passwords exposed in record-breaking data breach

The massive excitement around Artificial Intelligence (AI) tools has become a goldmine for cybercriminals. They’re heavily using this buzz to trick people into downloading dangerous ransomware and malware. This isn’t just a tactic for highly advanced hackers anymore; even smaller, lesser-known groups are now effectively using this strategy. These malicious actors, including ransomware gangs like […]
Cybercriminals Are Using Fake AI Tools to Spread Malware

The massive excitement around Artificial Intelligence (AI) tools has become a goldmine for cybercriminals. They’re heavily using this buzz to trick people into downloading dangerous ransomware and malware. This isn’t just a tactic for highly advanced hackers anymore; even smaller, lesser-known groups are now effectively using this strategy. These malicious actors, including ransomware gangs like […]
Over 16,000 Fortinet Devices Compromised with Symlink Backdoor

Security researchers have discovered that over 16,500 Fortinet FortiGate firewall devices have been compromised by attackers using a symlink-based backdoor. This attack allows persistent and stealthy remote access to affected systems. The discovery was made by Lexfo Security, and the infections are believed to have started as early as 2022. Despite patches being released by […]
Cybercriminals Are Evolving — And They’re Using AI Against You.

At PKF, we recognize that the cybersecurity landscape demands strategic vigilance, technical agility, and board-level attention. Microsoft’s latest Digital Defense Report outlines urgent trends that reaffirm what we’ve seen across industries: cyber risk is no longer a technical issue—it’s a business-critical concern. Here are the key highlights and what they mean for our clients and […]
SuperBlack Ransomware Exploits Fortinet Vulnerabilities for Unauthorized Access

A new ransomware group known as ‘Mora_001’ has been identified exploiting two authentication bypass vulnerabilities in Fortinet firewall appliances to deploy a custom ransomware strain named ‘SuperBlack’. Exploited Vulnerabilities: CVE-2025-24472: Initially fixed in January 2025, this vulnerability enables remote attackers to gain super-admin privileges by making maliciously crafted CSF proxy requests. Although Fortinet initially stated […]
Critical RCE bug in Microsoft Outlook now exploited in attacks

CISA Urges U.S. Federal Agencies to Secure Systems Against Critical Microsoft Outlook Vulnerability The Cybersecurity and Infrastructure Security Agency (CISA) issued a warning to U.S. federal agencies, urging them to secure their systems against ongoing attacks exploiting a critical remote code execution (RCE) vulnerability in Microsoft Outlook. This vulnerability, identified by Check Point researcher Haifei […]
Microsoft Thailand Collaborates with NCSC to Strengthen Cybersecurity in Thailand

Bangkok, Thailand – May 28, 2024 – Microsoft Thailand today announced a collaboration with the National Cyber Security Agency (NCSC) to join the Government Security Program (GSP) to exchange cybersecurity information, knowledge, and insights in a transparent manner, aiming to strengthen cybersecurity in Thailand. The Government Security Program (GSP) is a global initiative where Microsoft […]
PEGASUS: Cyber Warfare

‘T’was the night before Songkran, and all through the house, not a creature was stirring, except …” the Pegasus spyware working quietly and invisibly in the background on your devices and copying all your personal information and data to a computer server in some foreign country… while your sleep soundly in your bed, completely unaware […]
