Corporate Treasury Services

At PKF Thailand, we help companies identify and manage risks, improve financial performance, and unlock long-term value through insight-driven, technology-enabled solutions. We provide corporate treasury advisory services and, through partnering agreements with major treasury management system providers, leading edge technology solutions.
Google Patches Sixth Chrome Zero-Day Exploited in 2025 Attacks

Google has released an emergency security update to fix a new zero-day vulnerability in its Chrome web browser, marking the sixth actively exploited flaw patched this year. The Vulnerability Security Update Zero-Days in 2025 This latest fix adds to a growing list of Chrome zero-days exploited this year: In 2024, Google patched 10 additional zero-day […]
The Great Firewall Data Leak: A Global Wake-Up Call for Cybersecurity Governance

In a striking development that underscores the fragility of digital sovereignty, over 500 gigabytes of internal data from Geedge Networks—a key contractor behind China’s Great Firewall (GFW)—was recently leaked online. This breach has revealed not only the technical architecture of one of the world’s most sophisticated internet censorship systems, but also the broader geopolitical implications […]
Impact of Inventory Shortages or Surpluses on VAT and Corporate Tax in Thailand

For VAT-registered businesses in Thailand, preparing and submitting accurate VAT reports within three business days is mandatory. Among these reports, inventory reports are legally required on a monthly or annual basis.
PKF Thailand Transparency Report 2025

PKF Thailand is pleased to present our inaugural transparency report for the year ended 30 June 2025. It provides an overview of PKF Thailand’s operations and gives insight on the ownership and governance of our firm, and our approach to maintaining high quality standards in our audit and other services.
Companies or Juristic Partnerships Lending Money and Business Tax Issues

When a company or juristic partnership lends money to another party as part of its ordinary business operations, it is required to register for specific business tax
CVE-2025-43300 vulnerability :Understanding Apple’s ImageIO Framework

Introduction Apple’s ecosystem is well-known for its seamless user experience. One of the unsung heroes behind this smooth interaction with digital images is the ImageIO Framework. This framework provides developers with a standardized way to read, write, and process image files across iOS and macOS. While ImageIO makes handling images efficient and reliable, it is […]
Cabinet Approves One-Year Postponement of Employee Welfare Fund Contributions to October 1, 2026

Bangkok, August 26, 2025 In response to economic uncertainty and rising financial pressures on both employers and employees, the Cabinet has approved a draft labor regulation that postpones the commencement of contributions to the Employee Welfare Fund from October 1, 2025 to October 1, 2026
NCSA Urges Immediate Update to iOS 18.6.2 and iPadOS 18.6.2 Following Discovery of Critical Vulnerability
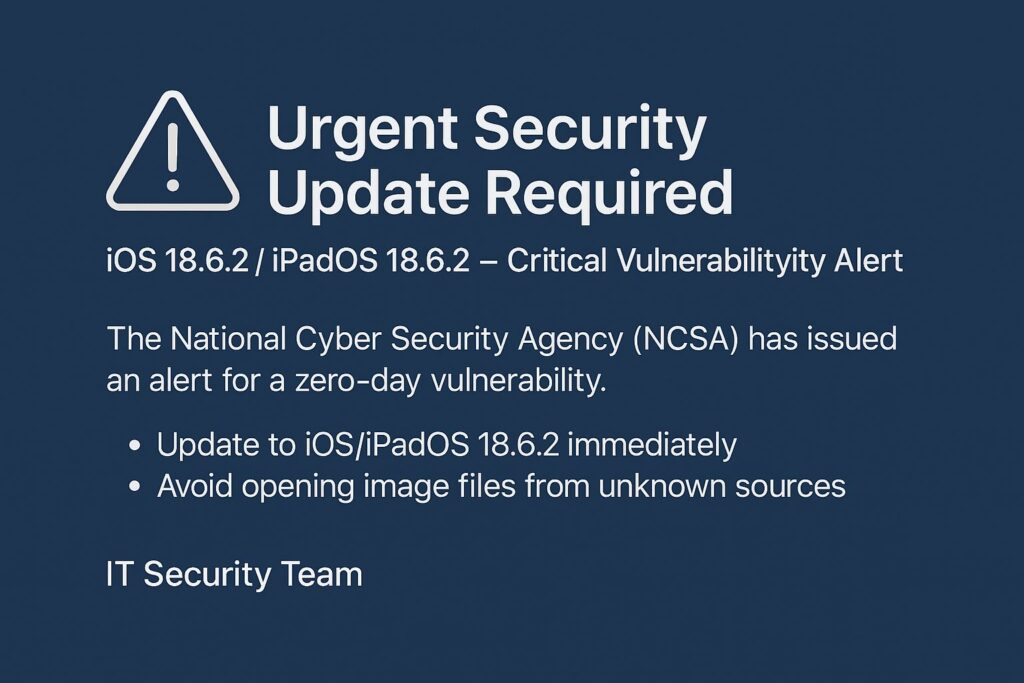
The National Cyber Security Agency (NCSA) of Thailand has issued an urgent advisory for all users of iPhone and iPad devices to promptly update to iOS 18.6.2 and iPadOS 18.6.2, following the identification of a critical security vulnerability tracked as CVE-2025-43300 within Apple’s ImageIO Framework. This vulnerability, classified as a zero-day, has reportedly been exploited in targeted attacks. According to Apple’s official security […]
Thailand BOI Announced Special Investment Measures to Promote Investors Relocating Production Bases from Cambodia

On 15 August 2025, Thailand Board of Investment (“BOI”) issued the Announcement No. 8/2568: Re Investment Promotion Measures in the Case of Impacts from Thai-Cambodian Border Situation.
